Configuring Provider Auth - Duo
For any customers leveraging provider auth, Cisco Duo is now an option as a 3rd party auth provider. Configure the OIDC connector as described in the duo documentation here:
https://duo.com/docs/sso-oidc-generic
Notes:
As with all 3rd party providers, user email addresses must match the Square 9 user accounts.
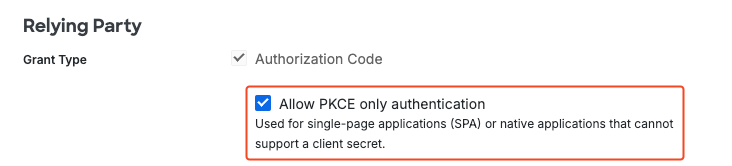
In the Relying Party > Grant settings, you must allow PKCE. This option is not enabled by default, so if you don’t make change, your authentication will fail.
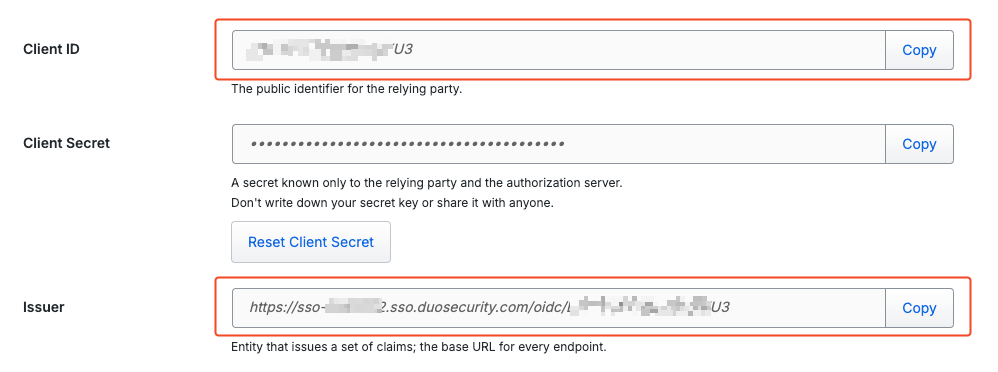
The client id and org url come from the application’s metadata config:
You must provide the appropriate redirect URL for any square 9 environments you wish to authenticate from. Note for GlobalSearch Go users: beta and stable have different redirects:
Stable - https://www.square9.cloud/login/redirect
Beta - https://beta.square9.cloud/login/redirect
GlobalSearch Web - https://<fqdn>/square9web/lib/oidc/oidc-callback.html
GlobalCapture Web - https://<fqdn>/square9captureweb/lib/oidc/oidc-callback.html
While enabled by default, OIDC response scopes should include openid, profile, and email.
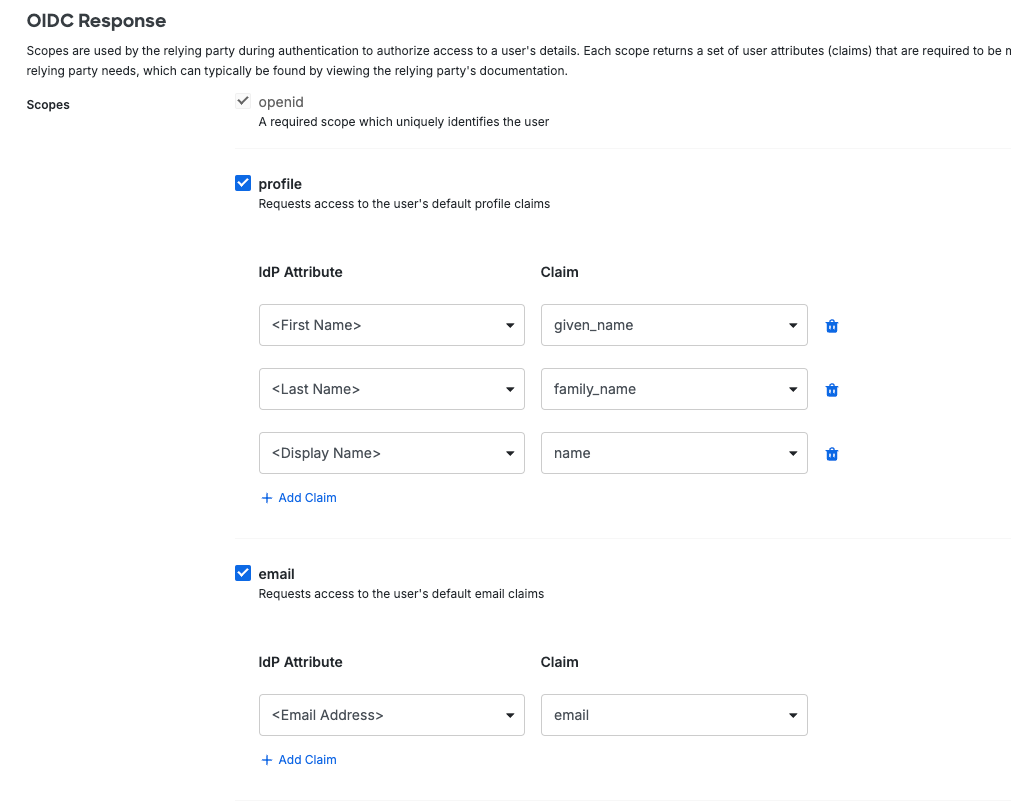
Be sure all noted settings are configured. Specifically grant types and oidc response scopes. Failure to configure these settings will result in failures that can be difficult to troubleshoot, so always double check these settings first.
